Guest post: The “Secure Platform” concept for Europe – a trusted and secure foundation for a human-centric digital world
Written by MyData Global member esatus AG
The following article discusses the technical requirements needed to protect our personal data and to ensure a safer digital world. It presents solutions for creating an open and secure IT infrastructure where data privacy can always be guaranteed. The article has been written by esatus, founding member and lead of the “Secure Platform” working group, a thematic group within the IT Security Association Germany (TeleTrusT). It was established in order to research and strengthen the concept of Digital Sovereignty for Germany and Europe, to protect the values of individuals and of society as a whole. The cooperation for this joint article between MyData Global and the “Secure Platform” experts reflects that both organisations share similar ideas. “Secure Platform” is fully consistent with the human-centric paradigm of MyData, where the sharing of personal data is controlled by the individual, and any manipulations shall be precluded.
With the steady acceleration of digital transformation, information technology has become an indispensable driver of societal well-being and is now omnipresent: whether we place an online order, follow a virtual business meeting or do our daily workout routine. Everywhere we leave traces of information about us, which means our personal data is everywhere. Due to the increasing number of digital accounts, we are losing track of our personal data and are unable to control how it is being processed by data-hungry big corporations. Cyber attacks and data leaks can threaten the very existence of companies, public authorities, or private individuals, as such incidents have a direct impact on their image and perceived trustworthiness.
When it comes to protecting our personal data and to monitor how they are being processed, the EU General Data Protection Regulation can be considered as a best practice example for data management. It is an essential prerequisite to ensure citizens can regain full control about their personal data. Among the fervent supporters of the EU data protection concept is the international non-profit organization MyData Global. Their aim is to empower individuals by improving their right to self-determination regarding their personal data.
Substantial progress has already been made in this respect, but there is still work to be done: how can data protection and IT security actually be implemented on the technical level, in such a way that is automatically enforced or built-in? Can our existing technological infrastructures ensure that these requirements are fulfilled?
How can data protection and IT security actually be implemented on the technical level, in such a way that is automatically enforced or built-in?
As set out above, a trusted and safe digital infrastructure will be needed to enforce protection of personal data. Such a platform can be seen as the stable and reliable technological foundation for the overarching concepts of data privacy and a human-centric view of the digital world. An essential prerequisite for such an infrastructure is digital sovereignty. Digital sovereignty plays a crucial role not only for the protection of our personal data and privacy, but also for Europe’s competitiveness, for Industry 4.0, or for projects such as GAIA-X and 5G. Digital sovereignty means that the EU must be able to independently protect the essential values of citizens, public authorities, and the economy. These values include not only private, professional, state and business secrets, but they also mean compliance with data protection and antitrust law, trust and reputation, as well as financial integrity and the integrity of physical assets and critical infrastructures. Everyone relies on the protection of these values. Today, we are still a long way from “digital sovereignty“ as there are dependencies on factors that we cannot control. These are discussed in the following paragraphs.
Dependency on external production and supply of technology
Nowadays, European companies hardly play a role as suppliers for widely used IT. In almost all areas the market-leading technologies are manufactured outside Europe. Asia and the USA are particularly dominant here. Each manufacturer is bound to the respective legal requirements and cultural ways of thinking of its country, and so there are serious differences worldwide. Be it in the assessment of the strength of the encryption to be used or the deliberate integration of “back doors”. Complete trustworthiness cannot be guaranteed with such components. But due to the lack of alternatives, they are still used everywhere.
Technologies used are complex “black boxes”
Current IT systems are multi-layered structures comprising hardware and software. What is more, program codes and detailed technical properties are not available for independent testing (“closed source”). Thus, it is not possible to determine whether a product merely provides the desired functionalities or whether there are weak points or hidden back doors for manipulation. These can be found at practically every level of the IT system, including the hardware, the built-in “chips”.
Sustainable IT security is not a decisive criterion for design and purchase of a product
The design and production of current systems are characterized by the paradigms of “maximum functionality” and “short time-to-market”. Once the product is on the market, security-relevant updates are neglected. On the buyer side, trustworthiness and security in the products are wrongly taken for granted. Systems with a demonstrably higher level of security do not attract user attention because low prices and convenience are the sole purchase criteria. This is evidenced by the increasing number of IT security incidents.
Accepting the status quo is not an option
Discussions with users show time and again that people rather downgrade their requirements to the existing offer instead of the other way around. However, due to the importance for Europe’s economic competitiveness and the EU’s role as a vanguard of data economy, we should not accept the existing situation.
It is neither realistic, necessary nor desirable to have all elements of a digital infrastructure developed and produced by European manufacturers. However, a promising and goal-oriented strategy is to have European providers occupy selected thematic fields.
Digital sovereignty can be regained through the following steps:
- Reduce digital dependence on non-European suppliers
- Abandon harmful design paradigms
- Support more responsible buyer behavior
This would immediately result in a higher level of security and increased trust in the deployed components, helping to regain digital sovereignty. The odds for this project are quite good in Europe: existing technology production could be expanded, and the use of secure systems could be incentivized. Extensive expertise, competence and experience in IT security already exist in various European countries. Accordingly, there is nothing to prevent Europe from establishing another lighthouse for secure systems in addition to the GDPR.
The trustworthiness of systems is a well-known challenge.
The renowned security expert Bruce Schneier paints a vivid picture of the existing paradox:
“Security is a lot harder than reliability. We don’t even really know how to build secure systems out of secure parts, let alone out of parts and processes that we can’t trust (…). Current security technologies are nowhere near good enough, though, to defend against these increasingly sophisticated attacks. So while this is an important part of the solution, and something we need to focus research on, it’s not going to solve our near-term problems.” [1]
This task must be addressed with top priority. To achieve this goal, essential solution components should be identified first, which are then primarily developed and supplied by EU-based suppliers, in order to realize seamless monitoring and control from production to the supply chain. Another essential aspect is the proof of trustworthiness by means of certificates. Systems are subject to constant development and improvement. Certifications at intervals of one or more years only provide a snapshot. Here, a continuous review of the respective systems in the sense of a dynamic attestation would make sense. Appropriate certificates, test procedures and technologies would have to be developed for this purpose.
The need to build trustworthy systems from untrustworthy components exists on a global level. Market opportunities for any viable solutions in terms of products and processes would be excellent.
Secure platform as a potential solution for a secure and reliable IT infrastructure.
“Secure Platform” – practical concept
The concept is based on the following five technical layers:
- Hardware, 2. Chip architecture 3. Operating system 4. Applications 5. Mobile services
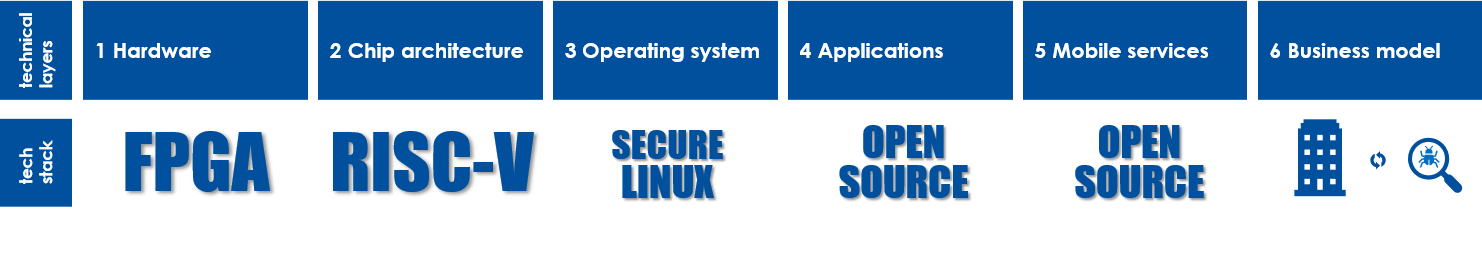
Figure – A practical model of a „Secure Platform“
There is a clear focus on defined functionality, easy usability, high to maximum security, resilient stability and adequate performance in line with the respective application. The concept of operation is seen as an additional layer, comprising – for the purpose of structuring – production, sales and support, with the aim to ensure a sustainable ongoing development of the platform, as well as dedicated security checks by independent institutions at regular intervals. The following design principles shall apply at all levels:
- Reduce complexity – „Principle of Least Technology”
“A Plea for Simplicity – You can’t secure what you don’t understand.” – B. Schneier. Principle to apply: Build a system with the minimum amount of components and codes that are actually required. - “Security by Design“
Time to market should not beat everything. A system can only be secure if security is considered as a design principle. Principle to apply: Integrate security in every component and at every level of the architecture. - Open architecture – „Open for transparency”
Closed architecture increases the risk of having weak points or hidden back doors for manipulation. Principle to apply: Offer all components as open source and ideally license-free, in order to be accessed and reviewed by anyone. - Security as a process – „Near-guaranteed Security“
Currently, the product life cycles are short and security updates are not planned. Principle to apply: Consider system safety as an indispensable product property that is permanently questioned and optimized during the life cycle. - Controlled Supply Chain – “A European Tech Supply Chain”
Currently, foreign technology dominates the IT market and might be a security risk. Principle to apply: Re-cultivate the IT production in Europe, so that technical components will be manufactured within European borders. This will ensure control of the supply chain and strengthen the European position in international competition. - Investment protection – “Long-term Availability and Compatibility”
Bringing systems up to date often requires complete replacement, with expensive migration projects. Principle to apply: Ensure long-term availability of system components and downward compatibility as a (largely) guaranteed goal. - Sustainability – “Reconfigurable Hardware”
Products are designed to fail after short lifetime. Principle to apply: Facilitate hardware reconfiguration during operating time, so that the hardware can be used longer. “Spectre & Meltdown” problems are either non-existent or can be solved. - Innovation – “Niche Technologies for the Masses”
Technology development follows well-trodden paths. Risk aversion dominates. Principle to apply: Bring disruptive technologies (such as FPGA) beyond the niche into practical application by end-users.
In addition to design criteria, security testing according to EU standards is desirable and promotes market success. Security-conscious organisations e.g. operators of critical infrastructures can be considered as a first target group.
Another promising approach towards trusted IT infrastructures is based on the concept of certificates that prove the trustworthiness of IT providers. MyData Global has initiated the MyData operator initiative, a voluntary commitment to support digital service providers of IT infrastructure for human-centric personal data management and governance. Organisations or companies that have been awarded with the MyData operator label commit to provide IT infrastructures that enable users to regain control over their personal data and to have full transparency about use of their data. MyData operators are key intermediaries in creating sustainable ecosystems for the fair and ethical use of personal data. The first MyData operators were awarded in 2020.
Regulations for personal data protection go hand in hand with the development of a trusted, secure IT infrastructure. Only by means of a joint effort can both data privacy and a human-centric view be ensured. The “Secure Platform” working group and MyData Global remain in constant exchange about current developments and look forward to further cooperation.
If you would like to support the Secure Platform concept for Europe and raise more awareness, please contact us – we would be happy to get back to you.
Join MyData Global as a member!
Author: esatus AG

References:
[1] https://www.nytimes.com/2019/09/25/opinion/huawei-internet-security.html
Copyright © 2021 esatus AG.
All rights reserved.
All content, photos and graphics are protected by copyright. No parts of this document shall be copied, reproduced, changed or transferred, in whole or in part without prior written consent of esatus AG.
Copyright: Michael Traitov/Adobe Stock


Pingback : Bet9ja Promotion Code 2021 * YOHAIG – Arctic Kingdom
Pingback : Piano Service Pro – Bet9ja Promotion Code >>> YOHAIG